Welcome back, my new hacker students!
As you may already know, hackers are now focusing on the Internet of Things
(IoT) more than ever. The IoT includes devices like routers, webcams, baby
monitors, Alexa, Google Home speakers, and even modern kitchen appliances—all
of which are connected to the internet.
These devices contain a small, basic computer inside, often running on a
version of Linux. While many systems have improved their security measures,
these devices are often left vulnerable, with many still using default
passwords.
In recent years, attacks like the Mirai DDoS attack have caused major
disruptions to the internet, affecting services like Twitter, Netflix, and
CNN. Attackers exploit these unprotected devices, compromising millions of
them to launch Distributed Denial of Service (DDoS) attacks. With so many
devices involved, no server or service is safe from these attacks.
Because these routers and devices have been used so effectively in DDoS
attacks, more attention is being paid to their security. To address this, a
tool called routersploit was created to bundle together the most effective
router exploits, similar to Metasploit. The developers have designed
routersploit's interface to resemble Metasploit's, making it easier for
those familiar with Metasploit to learn and use routersploit.
Download and Install routersploit
To download and install routersploit, you'll first need to install
python3-pip from the Kali repository. Here's how you can do it:
1. Install python3-pip:
apt-get install python3-pip
2. Download and install routersploit from GitHub:
git clone https://www.github.com/threat9/routersploit
3. Change directory to the new routersploit directory:
cd routersploit
4. Use the requirements.txt file to install routersploit requirements from
pip:
python3 -m pip install -r requirements.txt
5. Finally, start routersploit by entering:
rsf.py
This should get routersploit up and running on your system.
It's worth noting that routersploit displays its modules across the bottom of the screen, similar to Metasploit. It boasts 127 exploits, 4 scanners, 165 creds, 4 generic, and 21 payload modules.
Explore Routersploit
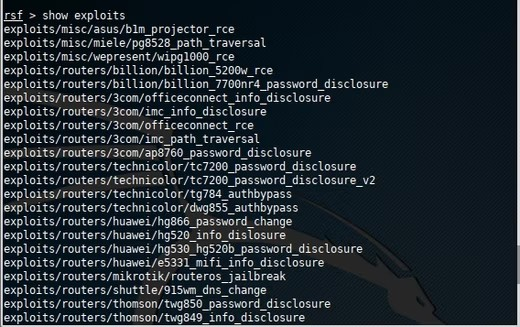
To explore routersploit, you can use the `show` command, just like in
Metasploit. If you want to see the available exploits, you would use the
command:
show exploits
As you can see, routersploit's 121 exploit modules are categorized by
manufacturer, model, and vulnerability. While this may seem like a large
number, considering the numerous router manufacturers and models, it
actually amounts to just a few per manufacturer. For example, there are 4
Huawei exploits for models HG866, HG520, HG530, and E5331. It's important
to find an exploit that matches your specific manufacturer and model.
To explore the available scanners in routersploit, you would use the
command:
show scanners
Search Function
Like Metasploit, routersploit also has a search function, although it's not
as advanced. In routersploit, you can search for modules using keywords, but
you can't specify the module type or platform like you can in Metasploit.
To search for modules containing the keyword "creds", you would use the
command:
search creds
This command will display all modules with the keyword "creds", as well as
some modules that contain the keyword "creds".
While you can't search by type or platform, a keyword search for the
manufacturer can be effective. For example, if your target router is
manufactured by "Linksys", you can enter the keyword "linksys" after the
keyword search to display all creds and exploit modules with "linksys" in
their names:
search linksys
If you're unsure which exploit to use and stealth isn't a concern,
routersploit has a module named autopwn that can test the router for
vulnerabilities. It's a scanner module. You can load it using the `use`
command, just like in Metasploit:
use scanners/autopwn
To view all the options and variables for this module, you can use the `show
options` command:
show options
This will show that you need to set the target IP, while leaving everything
else to the default settings:
set target 192.168.1.1
Once you've set the target IP address, you can simply enter `run` to execute
the scan, similar to Metasploit:
run
In this case, routersploit didn't find any vulnerabilities in the router but
did identify and display the default credentials.
If you can't exploit a vulnerability in the router, you might try getting
the credentials instead, as many IoT attacks happen this way due to default
credentials being left in place by users.
To see all the credential modules, you can use the command:
show creds
This will display numerous credential modules that target specific router
types and services such as FTP,
SSH, etc.
Let's try using a brute force creds module for HTTP basic digest
authentication to gain access to the router's admin panel:
use creds/generic/http_basic_digest_bruteforce
After loading the module, let's look at the options:
show options
This module requires entering the target IP address and has a built-in
password list. We'll use the default settings, but you could use any
wordlist from Kali or one you've downloaded by setting the passwords
variable to the absolute path to the wordlist.
Set the target IP address:
set target 192.168.1.1
To start the module, enter:
run
The module will begin trying all password combinations with the username
"admin". If successful, it will display the username and password,
indicating that the default credentials were left in place.
Summary:
Hacking the Internet of Things has become a significant focus for hackers,
with routers being a key target. Routersploit offers numerous modules for
router exploitation, although its search function could be more effective in
finding specific modules. Despite this limitation, Routersploit is a
valuable addition to a hacker's toolkit.
It's important to note that hacking into routers or any device without
authorization is illegal and unethical. The information provided here is for
educational purposes only. Always ensure you have permission before testing or
exploiting any system.