Social engineering involves using psychological tricks to deceive people into making security mistakes or revealing sensitive information. Attackers typically start by gathering information about their target, such as weak security points, and then build trust to manipulate them into compromising security.
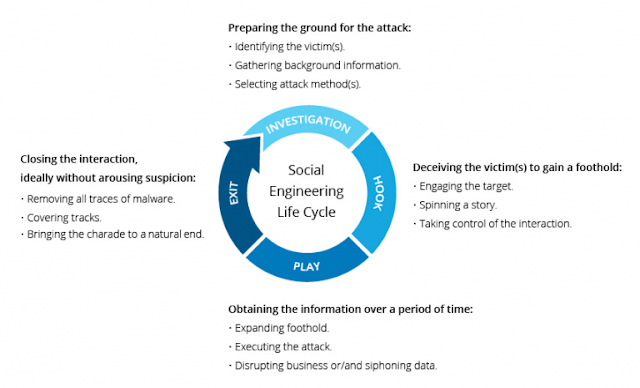 |
| Social Engineering Attack Lifecycle |
What makes social engineering particularly risky is that it exploits human mistakes instead of software or operating system vulnerabilities. Errors made by genuine users are less predictable and therefore more difficult to detect and stop compared to malware attacks.
Social engineering attack techniques
Social engineering attacks can take many forms and can happen wherever people interact. Here are five common types:
Baiting
This trick uses false promises to lure victims into revealing information or downloading malware. Attackers might leave infected USB drives in places where people will find them, like bathrooms or parking lots. When someone plugs the drive into their computer, it installs malware.
Scareware
Victims are bombarded with fake warnings about malware on their systems. They're tricked into buying useless software or installing malware. For example, you might see a popup claiming your computer is infected and offering to fix it if you download a program, which is actually malware.
Pretexting
Attackers lie to get information. They might pretend to be someone who needs sensitive information to do a job. They could impersonate a co-worker, police officer, or bank official to trick you into giving them personal data.
Phishing
Scammers send emails or texts that look urgent or alarming, prompting recipients to reveal sensitive information, click on malicious links, or open harmful attachments. For example, you might get an email saying your account has been hacked and asking you to click a link to change your password, which leads to a fake website that steals your login details.
Spear phishing
This is a targeted form of phishing. Attackers choose specific individuals or organizations and tailor their messages to make them seem more legitimate. For example, they might impersonate a company's IT consultant and send emails to employees asking them to change their passwords, directing them to a fake website to capture their credentials.
These attacks rely on human error, making them hard to detect and stop compared to attacks that target software vulnerabilities.
Social engineering prevention
Social engineers use feelings like curiosity or fear to trick people into falling for their scams. To protect yourself, be cautious of alarming emails, tempting offers online, or random digital media you find. Stay alert to avoid most social engineering attacks online.
Here are some tips to help you stay safe:
1. Don’t open emails or attachments from unknown sources: If you're unsure about an email, don't open it. Even if you know the sender but the email seems suspicious, verify the information through other means, like calling them or checking the official website.
2. Use multifactor authentication: This adds an extra layer of security by requiring more than just a password to access your account. It can protect your account even if your password is compromised.
3. Be cautious of tempting offers: If an offer seems too good to be true, it might be a scam. Do some research online to verify the offer before accepting it.
4. Keep your antivirus/antimalware software updated: Make sure your antivirus software is up to date to protect your system from infections. Enable automatic updates or manually update your software regularly.
Conclusion
Social engineering attacks are a significant threat in the digital world, exploiting human emotions and trust to manipulate individuals into divulging sensitive information or taking harmful actions. Awareness, caution, and the implementation of security measures such as multifactor authentication and keeping software updated are crucial in protecting oneself against these deceptive tactics. By remaining vigilant and skeptical of unsolicited communications and offers, individuals can significantly reduce their vulnerability to social engineering attacks.
