In the world of cybersecurity, there are many kinds of attacks and threats to computer networks. One of the most well-known types is social engineering attacks.
Whether you're an individual or an employee in a company, you're never completely safe from these attacks. They are commonly used by hackers to steal your sensitive information.
In a social engineering attack, the weakest point is not the computer system or the security software, but the people using them.
Luckily, social engineering techniques aren't only used by malicious actors. Security teams also use them to teach employees and staff how to avoid falling into these traps.
Today, we'll be looking at one of the most popular tools for social engineering: The Social Engineering Toolkit.
Disclaimer: The Social Engineering Toolkit (SET) is a tool designed for educational and ethical purposes only. It is meant to be used by security professionals to test the security of their own systems or with explicit permission from the owners of the systems being tested. The developers of SET are not responsible for any misuse or damage caused by the tool. Any unauthorized or malicious use of SET is strictly prohibited.
Table of Contents
What is the Social Engineering Toolkit? (SET)
The Social Engineering Toolkit (SET) is a popular cybersecurity tool created by Dave Kennedy from TrustedSec. It's used by security researchers, penetration testers, and security teams worldwide. Unlike other tools that target apps, SET focuses on tricking people into giving away sensitive information.
SET has many useful features, like faking phone numbers, sending fake SMS messages, and quickly creating phishing pages that look like real ones. Here are some key features:
- It works on Linux, Unix, and Windows.
- It can be customized with third-party modules.
- It has a user-friendly configuration menu.
- It includes access to the Fast-Track Penetration Testing platform.
SET offers various attack options, such as Spear-Phishing Attacks, Website Attacks, Infection Media Generator, Mass Mailing, Arduino-Based Attack, QRCode Attacks, Powershell Attack Vectors, and more.
Phishing Attacks:
This feature helps you craft convincing email messages with malicious attachments to trick recipients into revealing their information.
Web Attack:
This module includes options like Java Applet Attack and Metasploit Browser Exploit, which deliver malicious payloads to compromise remote victims.
Infectious Media Generator:
This option lets you create infected USB/CD/DVD devices that automatically run a malicious payload when inserted into a PC with autorun enabled.
Create a Payload and Listener:
This feature allows you to create various malicious payloads for Windows, including command shells and reverse connections.
Mass Mailer Attack:
This feature lets you send phishing emails to multiple recipients, including importing user lists and using Gmail or your own server for delivery.
Apart from these, SET also offers other attack options like Arduino-Based, Wireless Access Point, QR Code Generator, and Powershell Attack Vectors.
Now that you know about SET's features, you can install and test it for yourself.
Installation of Social Engineering Toolkit? (SET)
Installing the Social Engineering Toolkit (SET) is straightforward on most operating systems, especially Linux. Here's how you can do it on Linux distributions:
Update and upgrade your system:
apt update && apt upgrade
Install Git and Python if they're not already installed:
apt install git python
Clone the SET repository from GitHub:
git clone https://github.com/trustedsec/social-engineer-toolkit/ set/
Navigate to the SET directory:
cd set
Install the required dependencies using pip:
pip install -r requirements.txt
Once you've completed these steps, SET should be installed and ready to use on your system.
Usage of Social Engineering Toolkit? (SET)
After installing SET, you can run it from the command line by typing:
./setoolkit
You'll first see an agreement message; read it and accept it to proceed. After that, you'll likely see a welcome message, indicating that you're ready to use the tool.
After accepting the agreement, you'll see a menu displaying the most common options available in SET.
Selecting one of the options will display a full list of available attacks. For example, choosing option 1 might show you a menu like this:
1) Spear-Phishing Attack Vectors
2) Website Attack Vectors
3) Infectious Media Generator
4) Create a Payload and Listener
5) Mass Mailer Attack
6) Arduino-Based Attack Vector
7) Wireless Access Point Attack Vector
8) QRCode Generator Attack Vector
9) Powershell Attack Vectors
10) Third Party Modules
You can then select a specific attack from this list to proceed further.
Similarly, for other options, you can select the type of attack you want to perform and configure it accordingly.
For instance, let's look at phishing emails, a common social engineering method. To explore this in SET, you would go back to the main menu, choose option 5, and you might see a menu like this:
1) Mass Mailer Attack
2) SMS Spoofing Attack Vector
From here, you can select "Mass Mailer Attack" to proceed with setting up a phishing email campaign.
As shown, you can choose between emailing a single address or multiple addresses. For this example, let's choose the single email address option. After selecting that, you'll see a screen where you can begin setting up the phishing email attack.
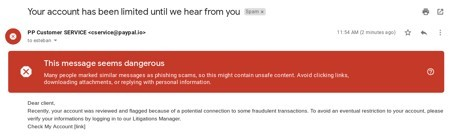
You used a phishing email example based on a real-world PayPal phishing attack to test the tool in your email test box. While your example may have lacked some formatting, it was a live test using the tool. A real attacker would likely put more effort into the email's style and text.
The email arrived successfully, but Gmail flagged it as spam and potentially dangerous, labeling it as a phishing scam.
Related Posts
Summary
The Social Engineering Toolkit offers a wide range of options for exploring different attack techniques. In this tutorial, we covered the installation process and some of the main features, demonstrating how simple it can be to execute a phishing attack using a fake email with a potentially malicious link.
There are many other aspects to explore, such as creating templates, generating malicious payloads, spoofing data, analyzing network traffic, and more.
With tools like SET, even users with basic technical skills can potentially carry out malicious attacks against organizations or individuals. It's important to remember that social engineering attacks rely not only on human psychology but also on gathering information about the victim.
Enjoyed this post? Share it with your friends and colleagues on social media! Your support helps us reach more people who could benefit from these insights. Have any thoughts or questions? Leave a comment below—I'd love to hear from you and continue the conversation!
FQAs
What is the Social Engineering Toolkit (SET)?
The Social Engineering Toolkit (SET) is a popular cybersecurity tool created by Dave Kennedy from TrustedSec. It is used by security researchers, penetration testers, and security teams to simulate social engineering attacks and test the security of systems.
What operating systems does SET support?
SET works on Linux, Unix, and Windows operating systems.
How do I install SET on a Linux system?
To install SET on a Linux system, update and upgrade your system, install Git and Python, clone the SET repository from GitHub, navigate to the SET directory, and install the required dependencies using pip.
What are some key features of SET?
Key features of SET include faking phone numbers, sending fake SMS messages, creating phishing pages, Spear-Phishing Attacks, Website Attacks, Infection Media Generator, Mass Mailing, Arduino-Based Attack, QR Code Generator, and Powershell Attack Vectors.
Can SET be used for malicious purposes?
SET is designed for educational and ethical purposes only. It should be used by security professionals to test their own systems or with explicit permission from the system owners. Any unauthorized or malicious use of SET is strictly prohibited.