Let's explore what BeEF, a web browser pen testing tool, is, what it's used
for, and how to start using it.
Editor's note: Tools like BeEF can be used in legal and beneficial ways by
security professionals, but they can also be misused for illegal and
unethical purposes. Ensure that your use of such tools is ethical, legal,
and in accordance with the law. If you're uncertain about the legality,
refrain from using them until you've done your research, which may include
consulting with legal counsel to discuss your plans.
Don't Miss: Install Kali Linux in Termux
What is BeEF?
BeEF is a tool that lets attackers take control of a web browser when
someone visits a malicious website. It's used to manipulate the browser and
carry out various attacks from within the browser itself.
For example, if a user clicks on a website controlled by an attacker, the
attacker can do things like show the user fake content, ask for permission
to access their microphone or webcam, try to run malicious code, or trick
the user into downloading malware. BeEF can simulate these attacks by taking
control of a browser tab that visits a website controlled by the attacker.
However, it's important to note that this control is limited. The attacker
can't control other tabs in the same browser or make requests to other
websites on behalf of the user. They can only redirect the user to websites
they control, send them links, or make them download malware.
What are the uses of BeEF?
At first glance, it might seem like a tool like BeEF is mainly for offensive
(red-team) cybersecurity activities. However, with some creative thinking,
there are ways it can be used by defensive (blue-team) cybersecurity efforts
too.
For instance, auditors could use BeEF to test and confirm the effectiveness
of zero-trust security measures. Zero trust means not automatically trusting
any device or user, even if they're within the network. BeEF can help by
showing how easy or difficult it is for an internal user to access a
resource compared to an external user, which is valuable information.
Another use could be in phishing tests. After a user clicks on a fake
malicious link as part of a simulation, BeEF could help analyze the
browser's behavior to understand potential vulnerabilities. Additionally,
BeEF could be used to check if your organization's browsers are properly
configured and secured against cyber threats.
Don't Miss: How to install Metasploit in Kali Linux
How to use BeEF
This tool can be easily installed on popular pen testing Linux distributions
like Kali and BlackArch. It comes pre-installed in some distributions or can
be installed using the default installation options. If you're using one of
these platforms, you can start using the tool quickly. Alternatively, you can
download a virtual machine (VM) image and run it. You can also obtain and run
the installer as you would with any other software.
After installation, using BeEF comes down to three main steps:
1. Planning your campaign
2. Hooking the browser(s)
3. Taking action on the objectives
Let's discuss each phase and look at examples of how to use BeEF for each one.
1. Planning Your Strategy
To start, you need a clear plan. This tool works best when you know exactly what you want to achieve. There are a few reasons for this. First, you need to get your target to visit a page you control. Often, you want this to happen without them realizing anything unusual is going on. Depending on your goal, you might use tactics like DNS poisoning, ARP spoofing, a watering hole attack, or persistent XSS. But you need to carefully consider how you'll do this.
Second, different browsers, operating systems, and settings can affect what you can do with BeEF. So, you'll need to be creative to reach your goal. Having a clear plan means you can make the most of opportunities that come up or use situations that might only last for a short time.1. Planning Your Strategy
To start, you need a clear plan. This tool works best when you know exactly what you want to achieve. There are a few reasons for this. First, you need to get your target to visit a page you control. Often, you want this to happen without them realizing anything unusual is going on. Depending on your goal, you might use tactics like DNS poisoning, ARP spoofing, a watering hole attack, or persistent XSS. But you need to carefully consider how you'll do this.
Second, different browsers, operating systems, and settings can affect what you can do with BeEF. So, you'll need to be creative to reach your goal. Having a clear plan means you can make the most of opportunities that come up or use situations that might only last for a short time.
Before you begin, ensure that the software is installed on your system. If you're using a platform like Kali Linux, the tool might not be installed by default, depending on your installation choices. Installing it is easy. For example, on Kali Linux, you can use the command below:
sudo apt update && sudo apt install beef-xssWhen you launch the software for the first time, it will ask you to create credentials. Remember these credentials, as you will need them later.
2. Hooking the browser(s)
Once you've planned your campaign, the next step is to execute it. You start by capturing one or more browsers using the tool. This process is simple: You embed specific scripts or code into a webpage and convince users to visit that page. It's important to be subtle to avoid detection. Various strategies, like phishing emails or persistent XSS, can be used to achieve this, especially during penetration testing.
After the software is loaded, you'll be prompted to log in to access the control panel, as shown in Figure 2. Use the credentials you set up for the software to log in.
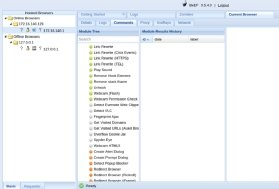
After logging in, you'll see a screen with basic information to get you started. It's important to read this carefully. You'll also see a list of web browsers that are connected. When you first open the software, no browsers will be connected, so you'll need to connect one.
To try it out, you can use the tool's demonstration pages. The code to connect a browser is simple and can be added to any webpage. Remember, you should only use this tool for legal purposes. Figure 3 shows the screen after connecting several browser tabs—one in a virtual machine (VM) and one outside a VM to show the difference.
Don't Miss: How to Install and Use Armitage on Kali Linux
3. Taking action on the objectives
After connecting one or more browsers, it's time to use them for testing or to achieve your goals. In the Commands section, you'll find actions you can take, color-coded for clarity:
Green: Commands that work on the target without the user noticing.
Red: Commands that don't work on the target.
Gray: Commands that might work but haven't been confirmed.
Orange: Commands that work but might be noticed by the user.
Experiment with these commands to see how they work. For example, to try the tabnabbing strategy, use the Redirect Browser option to direct the browser to a specific page. Simply enter the URL, click Execute, and the browser will redirect accordingly.
You can also monitor data users submit, view the pages they load, send them pop-ups, and fingerprint the browser. Spend some time exploring these options as you plan your campaigns.
The Proxy tab is another useful feature. You can create specific requests for the browser to retrieve or use the hooked browser as an HTTP forward proxy by right-clicking on it and selecting Use as Proxy. Keep in mind that browser rules apply, so it's most effective when testing pages on the same domain.
Additional features include XssRays for identifying XSS opportunities and the Network tab, which provides a map of the hooked browsers in relation to BeEF.
BeEF offers many ways to use the target's actions to gain access to the remote endpoint. It's about using creativity to achieve your desired outcomes.