How does D-TECT Works?
Using the D-TECT tool is straightforward. It's an automated tool, so after
running the d-tect.py file, a list of modules will appear. You just need to
select the module you want, like Subdomain Scanner or Port Scanner, and enter
the target domain URL (e.g., geeksforgeeks.org). The tool then gathers
information about the target and shows the results in a neat way on the
terminal. Make sure you have Python installed on your system since this tool
is based on Python.
Installation of D-TECT Tool on Kali Linux OS
Step 1: To install the tool on your Kali Linux operating system, use the
following command:
git clone https://github.com/shawarkhanethicalhacker/D-TECT-1.git
Example 1: Banner Grabbing
Select Option 1 to gather the banner information about the target domain
geeksforgeeks.org.
Example 2: Clickjacking Detection
Choose Option 5 to detect Clickjacking vulnerability on the domain.
Example 3: Port Scanner
Choose Option 4 to scan for open ports, which will then be displayed in the
screenshot below.
Example 4: WP Backup Grabber
Select Option 7 to perform a WordPress Backup Grabber, as shown in the
screenshot below.
Example 5: Sensitive File Detection
Select Option 2 to list critical files that may contain sensitive
information, as shown in the screenshot below.
Example 6: Cross-Site Scripting [XSS] Scanner
Select Option 6 to perform XSS scanning on the domain geeksforgeeks.org.
Example 7: SQL Injection [SQLI] Scanner
Select Option 8 to perform SQL Injection scanning on the domain
geeksforgeeks.org.
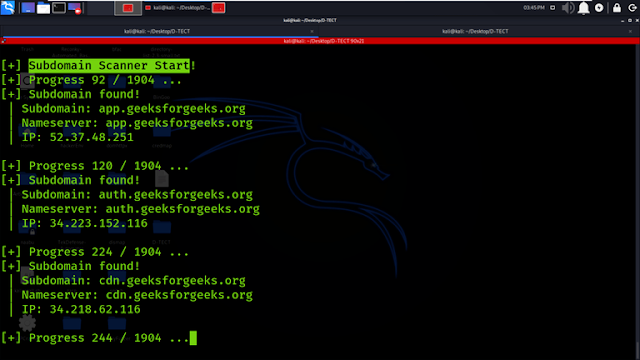
Example 8: Sub-domain Scanner
Select Option 3 to detect and display subdomains associated with
geeksforgeeks.org, as shown in the screenshot below.
Example 9: WP Username Enumeration
Select Option 1 to enumerate usernames associated with WordPress.
Example 10: Same Site Scripting Detection
Select Option 3 to perform Same Site Scripting vulnerability detection on
the subdomains of geeksforgeeks.org.
D-TECT is a powerful tool for automating the process of gathering information
and detecting vulnerabilities in web applications. Its features, such as
subdomain enumeration, port scanning, WordPress scanning, and detection of
vulnerabilities like XSS and SQL injection, make it a valuable asset for
security professionals. By following the steps outlined in this guide, you can
effectively use D-TECT to enhance the security of your web applications.